Zoom bombing interrupts student lectures
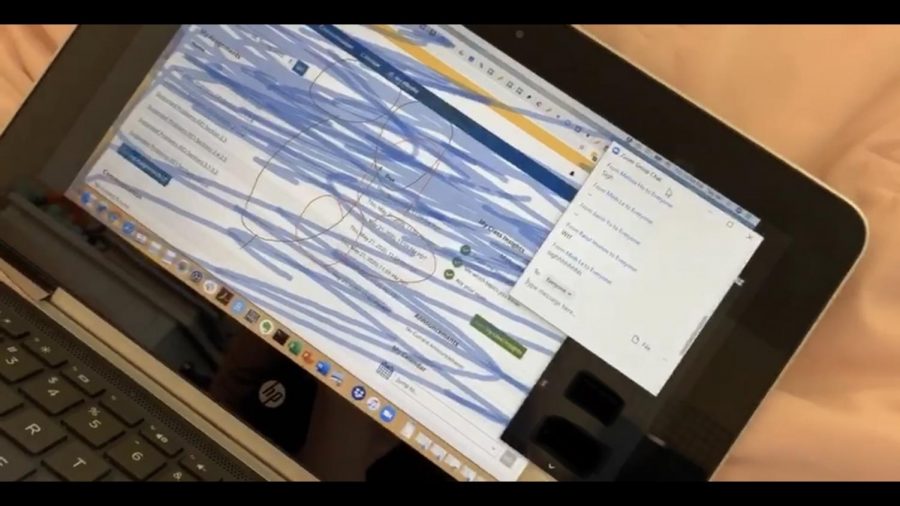
A screenshot of the video Yessenia Cuellar took of an individual interrupting her Zoom class session on April 2, 2020.
April 11, 2020
Yessenia Cuellar, a computer science major, was in her Probability and Statistics class when someone took over the screen and began digitally scribbling on the page. This faceless person also turned on their microphone to ask the professor to show her chest while drawing penises on the screen.
“I couldn’t read the text in time but like big things with random text and then someone started drawing all over the screen so the teacher ended it,” Cuellar said. “Then she posted again a Zoom meeting but this time with a password.”
Cuellar resumed the Zoom meeting with the new password but once the professor asked the class if there were any questions, the disrupters resumed interrupting the lecture.
“It’s quite possible that either someone in the class forwarded the link with the password in it to a disruptor, or, it in fact is a student is disrupting the session, or someone has access to a student account where the link is sent,” said Information Technology Officer Mary Morshed.
These interruptions are referred to as Zoom bombings, disrupters iinterrupt classes by including pornographic links, shouting or saying racial slurs and overall sharing their screen resulting in the professor or instructor ending the session.
With more classes relying on Zoom, which is free for SF State, these interruptions have become more of a concern. This has caused disrupters to join the lecture meetings with the intent to share inappropriate content.
“We see an average of anywhere from 500 to 1200 Zoom meetings initiated every day,” said Director of Academic Technologies Andrew Rodrick.
On April 7 Morshed sent an email on behalf of ITS and AT to staff announcing new security changes in order to mitigate interruptions.
“All meetings will include an auto-generated password in the link that prevents those not directly sent the official link from entering,” Morshed said.
“What has been reported into our support desks is that we’ve only seen three cases, which is a relatively small number of cases versus the number of meetings that are initiated on a daily basis,” Rodrick said.
Despite only receiving five reported cases thus far, AT has created a guide of best practices for Zoom security in meetings and sessions and advises faculty, staff and students to avoid hosting large meetings and distributing links publicly.
“The first thing we advise our faculty and instructors is to create their Zoom links within the iLearn environment so that they’re shared directly in the iLearn environment and initiated there and authenticated there,” Rodrick said.
Staff were also advised to host meetings so that only their screens were visible and require SF State credentials to login to view Cloud recordings.
“I’ve looked at some of the other CSU some of them are quite a bit more. I’m hoping we see less of this and put all necessary measures in place,” said Associate Vice President & Chief Information Officer Nish Malik.
Zoom bombing has made its way on Twitter user’s feed with videos of disrupters interrupting their lectures at other Universities.
“I just want to emphasize that we don’t take this lightly. We absolutely understand the disruption in the classes and the embarrassment it may cause to faculty and others,” Malik said.